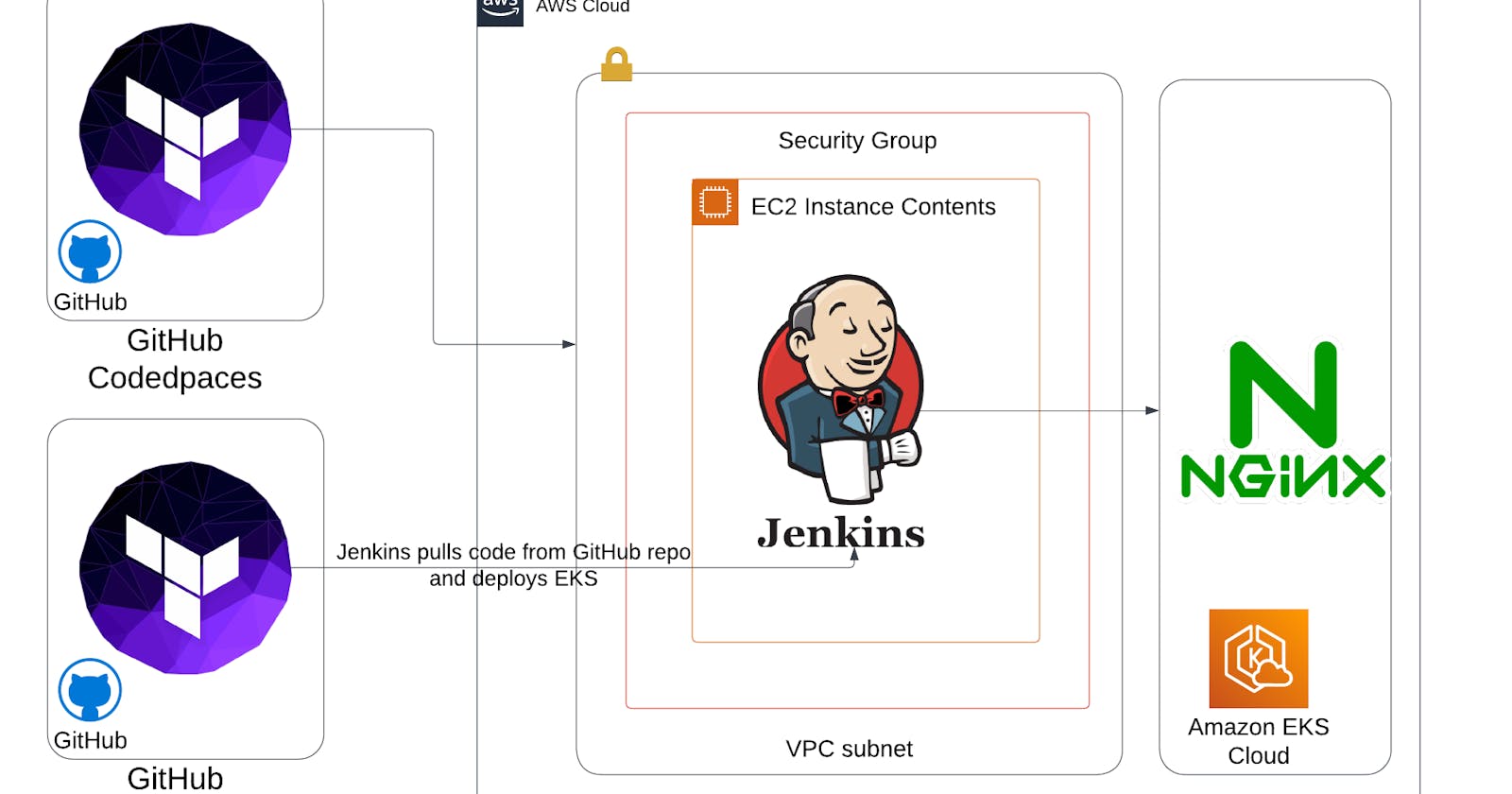
Project Overview: This project involves utilizing Terraform to provision essential resources such as a Virtual Private Cloud (VPC), Security Groups (SG), and Elastic Compute Cloud (EC2) instances. Additionally, Jenkins is deployed in that EC2 to automate the process. Jenkins, triggered by a GitHub webhook, retrieves another Terraform code to dynamically provision the infrastructure for Amazon Elastic Kubernetes Service (EKS). Furthermore, the configuration of an Nginx server within the EKS cluster is implemented as part of this project.
Github Repo:
https://github.com/Rupak-Shrestha/EKS-with-Terraform-CI-Jenkins.git
Created AWS account, configured MFA, added IAM user account with Administrator privilege, created alias for the account.
Create new github repo

Creating GitHub Codespace

Installing Terraform in Codespace
https://developer.hashicorp.com/terraform/tutorials/aws-get-started/install-cli
Configure AWS CLI
Create access keys
Install and Configure AWS CLI
#in terminal sudo apt install awscli -y aws configure #enter your access key ID and secret, and default regionCreate S3 bucket for Terraform backend

creating vpc, SG and EC2 for jenkins
terraform init terraform plan terraform validate terraform applyPush all code to GitHub repo
Resources created:
VPC
Subnets

InternetGateways

Security Groups

Jenkins deployed
Access jenkins

Get password here:
sudo cat /var/lib/jenkins/secrets/initialAdminPassword

Creating pipeline

Use GitHub webhook and configure pipeline to pull Jenkinsfile from GitHub repo.
pipeline {
agent any
environment {
AWS_ACCESS_KEY_ID = credentials('AWS_ACCESS_KEY_ID')
AWS_SECRET_ACCESS_KEY = credentials('AWS_SECRET_ACCESS_KEY')
AWS_DEFAULT_REGION = "ca-central-1"
}
stages {
stage('Checkout SCM'){
steps{
script{
checkout scmGit(branches: [[name: '*/main']], extensions: [], userRemoteConfigs: [[url: 'https://github.com/Rupak-Shrestha/EKS-with-Terraform-CI-Jenkins.git']])
}
}
}
stage('Initializing Terraform'){
steps{
script{
dir('eks'){
sh 'terraform init'
}
}
}
}
stage('Formatting Terraform Code'){
steps{
script{
dir('eks'){
sh 'terraform fmt'
}
}
}
}
stage('Validating Terraform'){
steps{
script{
dir('eks'){
sh 'terraform validate'
}
}
}
}
stage('Planning Terraform'){
steps{
script{
dir('eks'){
sh 'terraform plan'
}
}
}
}
stage('Creating EKS Cluster'){
steps{
script{
dir('eks') {
sh 'terraform destroy --auto-approve'
}
}
}
}
stage('Deploying Application') {
steps{
script{
dir('config-files/') {
sh 'aws eks update-kubeconfig --name eks-cluster'
sh 'kubectl apply -f deployment.yml'
sh 'kubectl apply -f service.yml'
}
}
}
}
}
}

Cluster created



Access nginx with the load balancer URL.

Happy Learning!